This article is an introduction to what is Cyber Kill Chain and how it works. Maybe if you follow some cybersecurity podcast, newsletter etc. you have heard about that, but did you know exactly what is it? Knowing what it is is mandatory for anyone wishing to approach any field of cybersecurity. So let’s start with a brief introduction and then go through all the steps.
What is Cyber Kill Chain?
Organizations of all sizes face the threat of cyber attacks. These attacks can come from a variety of sources, including nation-states, criminal organizations, and lone individuals. The goals of these attacks can also vary:
stealing valuable data
disrupting operations
causing physical damage.
To better understand the dynamics of these attacks, security experts have developed the “cyber kill chain” model. This model describes the various stages of a typical cyber-attack, from initial reconnaissance to post-exploitation. Organizations can develop more effective defences against these threats by understanding the kill chain.
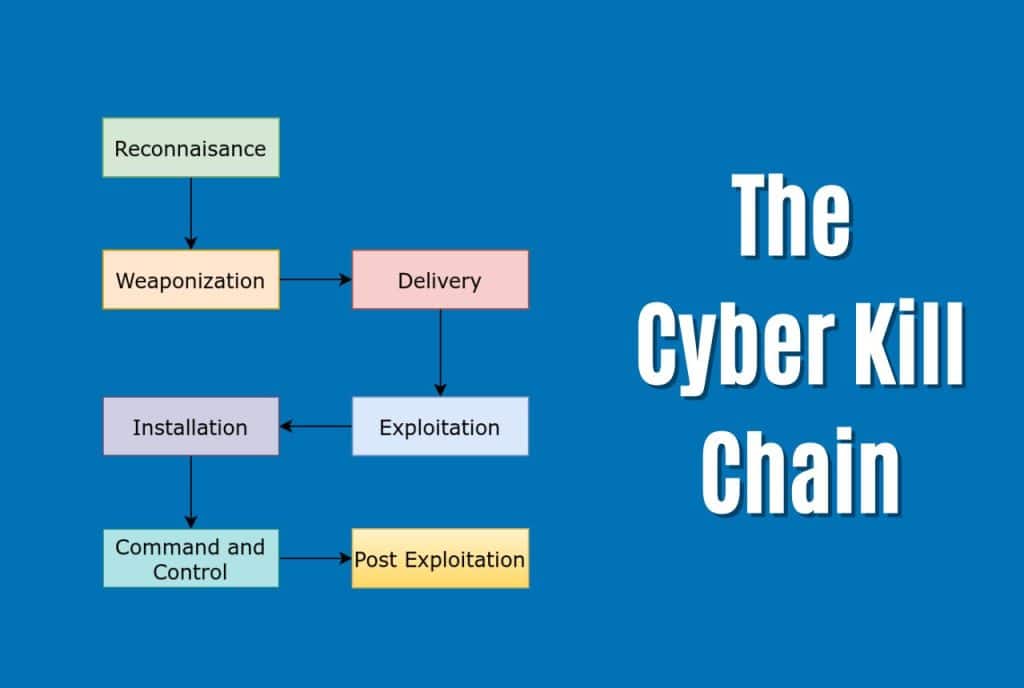
Stage 1: Reconnaissance
The first stage of the kill chain is reconnaissance. In this stage, the attacker gathers information about the target organization and its systems. He can obtain this information through open-source intelligence (OSINT) techniques, such as searching the internet or social media. He can also use more direct methods, such as social engineering or physical surveillance. The goal of reconnaissance is to gather enough information to plan and execute a successful attack. This information can include the names and titles of employees, the organization’s structure, and the types of systems and software in use.
One of the most important tools during this phase is Google itself, in fact, hackers use a technique called Google Dorking which can give as a result some useful information.
This phase is extremely important and may decide the life or death of the entire chain.
There are many tools that hackers use but here I just list the more famous just to have an idea.
Passive:
Google: as we’ve seen previously Google’s queries can be manipulated through Dorking in order to get all information a hacker needs.
Wireshark: Probably the best traffic analyzer.
Shodan: Search engine for IoT
Active:
Nmap: A powerful network scanner that is able to retrieve an enormous quantity of information from the target network/host
Nikto: A web server vulnerability scanner.
Subfinder: it’s a subdomain finder, very popular among hackers and pen-testers.
Maltego: Information gathering tool with a very intuitive Graphical interface.
We also built this blog with two basic tools for Reconnaissance:
Stage 2: Weaponization
In the second stage of the kill chain, the attacker creates or acquires the tools necessary to carry out the attack. These tools can include malware, exploit code, and phishing templates. The attacker may also need to purchase or rent access to a botnet, which can be used to launch distributed denial-of-service (DDoS) attacks.
As you can imagine that is a very sensitive phase and would be impossible to accomplish with bad Reconnaissance.
Useful resources in this phase are these:
Metasploit: It’s a very popular penetration testing framework, and contains a lot of exploits.
The framework includes a tool called MSFVenom that can generate very specialized payloads.Exploit-DB: It’s a database that contains a plethora of exploits for known vulnerabilities, a real gold mine for hackers.
AFL++: An open-source Fuzzer that can be used, when there are no known exploits, as a last resort to find zero-day on the target application.
The final goal of the hacker is usually the installation of malware in the target machine, so in addition to writing the exploit, malware development also belongs to the weaponization phase.
The hardest part is to make it invisible to the target’s security system.
Hackers can rely on tools like Veil3.0 or write their own code by hand.
We have seen some very basic techniques to hide shellcodes and some very basic evasion techniques that can make analysis harder.
Stage 3: Delivery
The third stage of the kill chain is delivery. In this stage, the attacker sends the weaponized tools to the targeted organization. There are a variety of methods that can help the attacker to accomplish the task, including email, social media, and physical media.
When the hacker doesn’t find a vulnerability, instead of wasting more time on that, can try to use social engineering and leverage the weak chain’s ring.
Even in this case, the reconnaissance stage can be very useful, for example, try to imagine how credible an email could be once a hacker has a flood of data on employees, companies, and used technologies.
Stage 4: Exploitation
The fourth stage of the kill chain is exploitation. In this stage, the attacker uses weaponized tools to gain access to the target system. This can be done by exploiting a vulnerability in the system or by tricking a user into entering their credentials. Once the attacker has gained access, they can then move laterally to other systems on the network.
Stage 5: Installation
In the fifth stage of the kill chain, the attacker installs malware on the target system. This malware can be used to further exploit the system or to exfiltrate data. The attacker may also use the malware to establish a persistent presence on the system, which can be used to launch future attacks.
Stage 6: Command and Control
The sixth stage of the kill chain is command and control (C2). In this stage, the attacker establishes a communication channel with the malware on the target system. The hacker can use this communication channel to issue commands to the malware and to exfiltrate data from the system.
The channel can be anything, and the malware writer will try to mask the traffic as much legitimate as possible, here a conference paper where you can read a study about using social media in order to control botnets.
Stage 7: Actions on Objectives or Post Exploitation
The seventh and final stage of the kill chain is actions on objectives or post-exploitation. In this stage, the attacker carries out their desired actions, such as stealing data or disrupting operations. Once the attacker has achieved his objectives, he may choose to cover his tracks or launch additional attacks.
Conclusion
The cyber kill chain is a helpful model for understanding how hackers carry out cyber attacks. By understanding the various stages of the kill chain, organisations can develop more effective defences against these threats.
Even if you can find many versions of Cyber Kill Chain online, they are all quite similar and probably they are all right. What is important to understand is the basic idea and the hacker’s working flow.
Said that it can also be useful for a pen-tester to plan his work as best as possible (reasoning as a black hat is the only way to make a good job).
I hope you enjoyed the article, If yes keep following me and I won’t let you down.
