Why use a Cybersecurity Lab?
A cybersecurity lab is a safe environment where you can experiment with new tools and techniques without affecting your production systems.
It is a place where you can test your defences and find weaknesses before an attacker does.
It is also a great place to learn about new technologies and hone your skills.
Many of the tools and techniques you will use in a lab are the same ones you will use in the real world.
What do you need to set up a Cybersecurity Lab?
In order to have a good and working cybersecurity lab you don’t need so much:
The first thing you need is a computer with enough processing power and memory to run multiple virtual machines.
The second thing you need is virtualization software. This software will allow you to run multiple virtual machines on your computer.
There are many virtualization software options available, but I recommend using VirtualBox.
This article will be a step-by-step guide on how to install Virtualbox in Windows with relative screenshots.
Whatever kind of lab you need, the first step is to install virtualization software, Virtualbox in this case!
What is VirtualBox?
Oracle VM VirtualBox is a general-purpose, open-source, and powerful virtualization software that allows users to install and run multiple guest operating systems (OS) like Windows, Linux, BSD, OS/2, Solaris, Haiku, and OSx86.
VirtualBox makes it possible to quickly install and run the operating system without requiring using dedicated hardware resources. It is commonly used as a server, desktop, testing environment, or learning how-to use tools.
Cybersecurity experts use VirtualBox for testing, training, and practising cybersecurity techniques. It has Graphical User Interface (GUI) that makes it easier to deploy the desired setup within a few seconds. VirtualBox provides the service to deploy operating systems or servers from ISO images or from VDI/VMDK/VHD images.
It makes it easier for users to install required servers or operating systems as it can run both GUI setups as well as CLI setups.
Moreover, VirtualBox has no limitation for the deployment of the maximum number of guests.
First, download VirtualBox and then install it
You can click https://www.virtualbox.org/wiki/Downloads or go to Google and search for “Download VirtualBox for Windows”.
The website offers multiple platform packages, but we need to download the one that suits our Windows version. So, please click ‘Windows Hosts’. It will automatically start downloading.
Once the download has been completed, you should Right-click setup and click “Run as an administrator”
Install VM VirtualBox
Oracle VM VirtualBox Setup will appear. The installation process is quite simple. Just click the ‘Next’ button.
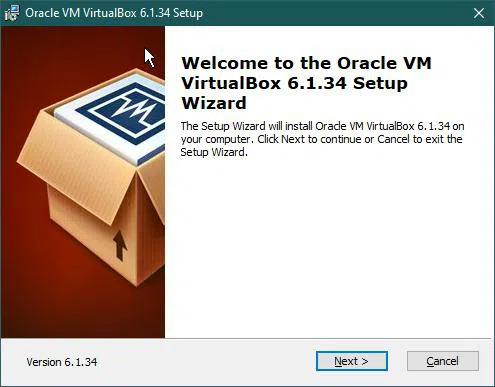
Here, you can select your desired features. However new users can keep the default settings without problems.
So let’s click the ‘Next’ button.
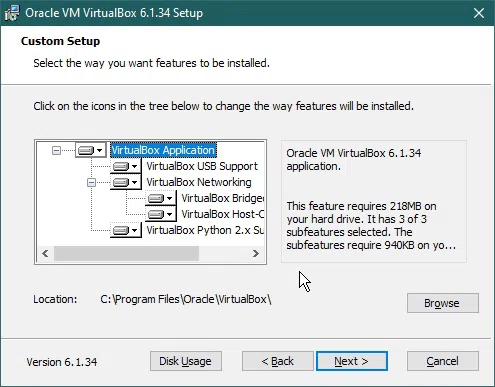
After that, we can customize shortcuts for accessing VirtualBox.
I recommend, that when you install Virtualbox for the first time, don’t change the default settings.
If you need, everything can be changed in the future.
So click the ‘Next’ button.
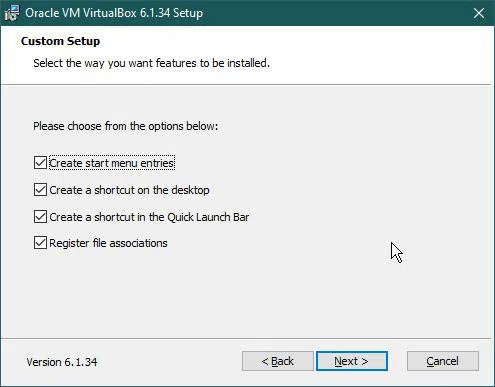
Again we’ll proceed with default settings.
After that, the installer will warn us that it’s going to restart the connection, let it do it.
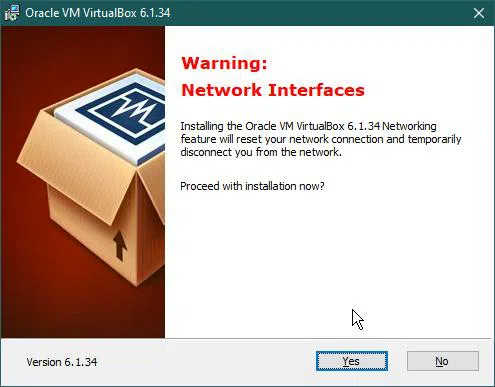
Now the setup configuration is done and we are ready to install VirtualBox software.
Click ‘Back’ for reviewing /changing installation settings, or ‘Cancel’ to exit the wizard.
Click ‘Install’ to start the installation of VM Virtualbox,
The setup will start installing VM VirtualBox. It may take 5 to 10 minutes.
Finally, Oracle VM VirtualBox Installation is complete.
At this point, you can select the option to start VM VirtualBox after installation and click ‘Finish’.
Anyway, if you want to stop there, next time, you can launch VirtualBox by double-clicking the desktop shortcut.
Conclusion
Installing a virtual machine is the first step to setting up a cybersecurity lab for many reasons:
It is the quickest and easiest way to set up a lab.
It is the most efficient way to create and destroy machines.
It is the most convenient way to control and automate the creation of machines.
It is the most convenient way to share and distribute machines.
You can easily take and restore a snapshot
And many more.
In future articles, I’ll show you how to install other software for different use cases.
However, all of them will need a virtual machine.
